This blog is about understanding, auditing, and addressing risk in cloud environments. Systems and architectures are rapidly converging, hiding complexity with additional layers of abstraction. Simplicity is great for operations - as long as risks are understood and appropriately addressed.
Sunday, November 5, 2023
IT Audit Process - Review
Thursday, October 19, 2023
Navigating the Waters of Change
This information was gathered to help people at VMware as many prepare for the pending Broadcom acquisition by Lorelei Ghanizadeh Voorsanger | LinkedIn. Thank you, Lorelei, for sharing with so many others that need this information. You are a blessing. And thank you to the hundreds of people that have reached out to me and my peers with resources and help. You are appreciated.VMware peers, you are seen. Reach out to me. I have a lot of resources that may be helpful.
Update Your LinkedIn Profile
- Consider verifying your LinkedIn profile.
- Get a nice professional looking headshot: Take professional headshots at home.
- Update your tagline using, e.g. "position | keywords | mission (optional)"
- Update your background picture. Consider www.canva.com. Several free designs.
- Ask for letters of recommendation: Request a recommendation on LinkedIn
- Notify recruiters (and optionally your network) that you are open to opportunities
- Add your resume to your profile: Add profile section | Recommended | Add featured | + | Add media
Improve Your Resume
- Rezi: Rezi - The Leading AI Resume Builder
- TealHQ: Free AI Resume Builder (tealhq.com)
- Jobscan: Free Resume Templates for 2023 (jobscan.co)
- MS Word: File | New | Search for Online Templates | Resume
- Etsy: ATS Compliant Resume - Etsy
- Adobe: Free resume builder
- Grammer Check: Grammarly: Free Writing AI Assistance
- NovoResume: Free Resume Templates for 2023 (novoresume.com)
- OpenAI: ChatGPT
- Coverdoc.ai: AI-powered cover letter writing & research assistant
- Indeed: Free Cover Letter Templates | Indeed.com (great primer/discussion as well)
The AWS Cloud Resume Challenge
Manage the Job Search
Application Tracker
- Job Search Spreadsheet by The Muse on Google Sheets
- Huntr Job Search Tracker and Autofill from Google Chrome
Job Search Sites & Placement services – US-centric
- Indeed
- Glassdoor Jobs
- HiringCafe
- Monster
- ZipRecruiter
- SimplyHired
- CareerBuilder
- Jobs and talents in InfoSec / Cybersecurity | infosec-jobs.com
Practice Interviews
- Common Interview Questions | LinkedIn (pay attention to the categories)
- InterviewPrep AI
- Yoodli.AI
Manage the Offer
- Harvard Business Review’s 15 Rules for Negotiating a Job Offer
- TheMuse’s How to Negotiate Salary: 37 Tips You Need to Know
- MoneyGeek’s The Ultimate Guide to Negotiating Your Salary
Wednesday, September 20, 2023
PCI DSS Vulnerability Scanning and Penetration Testing Hygiene
 |
| Image: Dalle3 |
Vulnerability Scans (11.3.1.3 and 11.3.2.1)
One of the critical security controls that PCI DSS v4.0 emphasizes is the need for internal vulnerability scans. Companies must perform these scans after any 'significant change,' as defined by the standard. Significant changes include things like adding new hardware, software, or making considerable upgrades to existing infrastructure.
The scans aim to detect and resolve high-risk and critical vulnerabilities based on the entity’s vulnerability risk rankings. Following the scan, any detected vulnerabilities must be resolved, and rescans should be conducted as needed.
External vulnerability scans are equally important and follow the same triggering mechanism—significant changes in the environment. Here, the focus is on resolving vulnerabilities scored 4.0 or higher by the Common Vulnerability Scoring System (CVSS). As with internal scans, rescans are required as necessary to confirm that vulnerabilities have been adequately addressed.
Penetration Testing (11.4.2, 11.4.3)
Internal penetration testing is a more aggressive form of evaluation and should be conducted at least once every 12 months or after any significant change to the infrastructure or application. The testing can be carried out either by a qualified internal resource or a qualified external third-party, provided that there is organizational independence between the tester and the entity being tested. Notably, the tester doesn't need to be a Qualified Security Assessor (QSA) or an Approved Scanning Vendor (ASV).
Much like its internal counterpart, external penetration testing is required annually or after any significant alterations to the system. The testing must also be conducted by qualified resources and should follow the entity’s defined methodology for testing.
What Constitutes a 'Significant Change'?
PCI DSS v4.0 is pretty broad in what it considers to be 'significant changes,' effectively encompassing any new hardware, software, or networking equipment added to the Cardholder Data Environment (CDE), as well as any replacement or major upgrades to existing hardware and software in the CDE. The list is exhaustive and is aimed at ensuring that any changes, no matter how seemingly minor, are given adequate attention from a security perspective.
Summary of Requirements
The PCI DSS v4.0 requirements for vulnerability scans and penetration testing provide a structured approach for entities to keep their data environments secure. While these requirements might seem stringent, they offer a well-defined framework for securing cardholder data against the backdrop of ever-advancing cyber threats. Adhering to these requirements is not just about ticking compliance boxes; it’s about taking the necessary steps to protect your organization and its stakeholders.
- Internal
vulnerability scans:
- 11.3.1.3
Internal vulnerability scans are performed after any significant
change as follows:
- High-risk
and critical vulnerabilities (per the entity’s vulnerability risk
rankings defined at Requirement 6.3.1) are resolved.
- Rescans
are conducted as needed (significant changes..).
- External
vulnerability scans:
- 11.3.2.1
External vulnerability scans are performed after any significant
change as follows:
- Vulnerabilities
that are scored 4.0 or higher by the CVSS are resolved.
- Rescans
are conducted as needed (significant changes..).
- Internal
penetration testing:
- 11.4.2
Internal penetration testing is performed:
- Per
the entity’s defined methodology, at least once every 12 months
- After
any significant infrastructure or application upgrade or change
- By a
qualified internal resource or qualified external third-party
- Organizational
independence of the tester exists (not required to be a QSA or ASV).
- External
penetration testing:
- 11.4.3
External penetration testing is performed:
- Per
the entity’s defined methodology, at least once every 12 months
- After
any significant infrastructure or application upgrade or change
- By a
qualified internal resource or qualified external third party
- Organizational
independence of the tester exists (not required to be a QSA or ASV).
- Significant
changes are defined in PCI DSS to include (PCI-DSS-v4_0.pdf page 26):
- New
hardware, software, or networking equipment added to the CDE.
- Any
replacement or major upgrades of hardware and software in the CDE.
- Any changes in the flow or storage of account data.
- Any changes to the boundary of the CDE and/or to the scope of the PCI DSS assessment.
- Any changes to the underlying supporting infrastructure of the CDE (including, but not limited to, changes to directory services, time servers, logging, and monitoring).
- Any changes to third party vendors/service providers (or services provided) that support the CDE or meet PCI DSS requirements on behalf of the entity.
Thursday, September 14, 2023
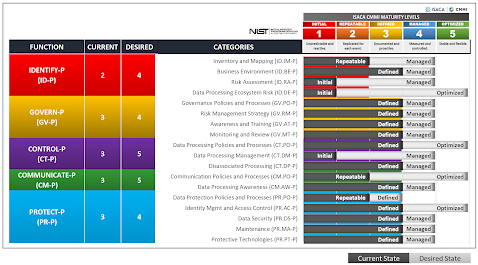
Using Maturity Levels and Qualitative Measurement for Visualizing Technology Implementations
Check out this maturity model. What does it mean to measure the maturity of a technology implementation qualitatively? And how can maturity levels help visualize the current and future states to meet control requirements?
Let's unpack these concepts and show how qualitative measures can enrich the maturity model process, particularly with the use of visualization techniques like bar or radar graphs.
Maturity models serve as diagnostic tools, usually consisting of a sequence of maturity levels that provide a path for improvements. These models are vital for benchmarking and identifying the best practices that need to be implemented for organizational success. In technology implementation, they can gauge how effectively an organization is meeting its control requirements—be it in data security, governance, or software development lifecycle.
The Qualitative Dimension
While numbers and metrics provide a certain level of clarity, they often lack context. Qualitative measurements step in here to provide nuanced insights into otherwise cold data. Through expert interviews, case studies, and scenario analyses, qualitative assessments can address 'how' and 'why' questions that numbers cannot.
One of the powerful ways to present the qualitative aspect of maturity models is through visualization. A bar or radar graph can be used to overlay the current and future states of an organization's maturity levels.
Current State
Imagine a bar graph where the X-axis represents different control requirements like "Data Encryption," "User Access Management," and "Compliance Monitoring," and the Y-axis represents maturity levels from 0 (Non-existent) to 5 (Optimized). The current state can be represented by blue bars reaching up to the current maturity level for each control requirement.
This visualization allows stakeholders to immediately grasp which areas are well-managed and which need improvement. It's not just about the height of the bar but the story behind each bar—which can be enriched by qualitative inputs like expert opinions, employee feedback, and process reviews.
Future State
In the same graph, future state scenarios can be represented by a different color—say, green bars—overlaying or adjacent to the current state bars. These future state bars are not arbitrary but are informed by qualitative measures like scenario planning, risk assessments, and strategic discussions.
The juxtaposition of current and future states in one graph offers a compelling narrative. It shows where the organization aims to be, providing a clear vision for everyone involved.
Utility of Qualitative Maturity Models
Maturity levels, when fleshed out with qualitative measurements, offer more than a snapshot of the present; they provide a roadmap for the future. Visual representations like bar or radar graphs give life to these qualitative insights, making them easy to understand and act upon.
So, the next time you consider assessing your organization’s technology maturity, think beyond numbers. Look at the stories those numbers can tell, and use qualitative measures to fill in the gaps. And don't just keep these insights in spreadsheets and reports—visualize them.
Combine qualitative measures with visualization techniques and build a more meaningful, actionable, and comprehensive roadmap. Aim for a balanced, nuanced, and visually engaging approach to understand the current state and opportunity for improvement.
Example Output
Here's a quick assessment of an organization's adherence to the NIST Privacy Framework. The beauty of this method - by the way - is that it's fast and easy to create this chart using qualitative measures. Search for the Privacy Framework spreadsheet under the downloads section if you want a copy of this.
Tuesday, September 5, 2023
NIST.SP.800-66r2.ipd Worksheet - HIPAA Indexed on NIST
Friday, September 1, 2023
Numbers and Narratives: The Power of Qualitative and Quantitative Feedback
The Quantitative Dimension
In the realm of cybersecurity learning programs,
quantitative data acts as the backbone that offers empirical evidence of
program effectiveness. This data, collected through various channels—from
real-world cybersecurity incidents and metrics on employee reporting to
targeted simulations and longitudinal studies—provides a measurable barometer
of your organization's cybersecurity posture. It can also help tailor training
materials to specific departments, evaluate ROI, and keep content up to date.
This section will detail the key types of quantitative data that you should
focus on, offering a robust framework for continuously enhancing your cybersecurity
initiatives through actionable metrics.
- Cybersecurity Incident Data - Utilize real-world data on past incidents to simulate realistic scenarios in your training programs. For example, if there has been a rise in phishing attacks, including similar scenarios in your learning modules can help prepare the workforce better.
- Metrics on Incident Reporting - Review how many employees report potential cybersecurity events pre- and post-training. An increase in reports post-training could indicate higher awareness.
- Simulated Attack Responses - Phishing simulations can provide invaluable data. If 90% of your employees ignore a phishing email post-training compared to 50% pre-training, you know you’re on the right track.
- Longitudinal Data - Track the program's impact over time to identify trends. Maybe the initial spike in awareness drops after six months, indicating a need for refresher courses.
- Employee Testing Data - Compare employee cybersecurity test scores before, immediately after, and three months post-training to assess knowledge retention.
- Performance by Department - Do tech departments outperform sales in cybersecurity awareness? This could guide department-specific training.
- Training Attendance and Completion Rates - Low attendance or completion could indicate that the training is too cumbersome or not engaging enough.
- Quantitative Surveys and Costs - Use closed-ended surveys for quick, quantifiable feedback. Also, calculate the per-participant cost of developing and delivering the program for ROI assessment.
- Privacy and Technical Metrics - Track the frequency and type of privacy or cybersecurity events to identify the need for role-based training. Changes following technical training—like a reduction in accounts with privileged access—can also be invaluable metrics.
The Qualitative Dimension
While quantitative metrics provide the hard facts, it's the
qualitative data that enriches our understanding by adding context, nuance, and
depth to these numbers. Qualitative feedback captures the human elements that
are often overlooked in cybersecurity initiatives. From capturing employees'
responses about the program's delivery and content to conducting focus groups
for in-depth insights, qualitative data allows us to gauge the intangibles that
make or break a learning program. In this section, we will delve into various
types of qualitative feedback, including presenter evaluations, open-ended
surveys, and even observations from the training sessions, to provide a more
holistic assessment of your cybersecurity education efforts.
- Presenter and Program Feedback - Encourage employees to share feedback on trainers and program content to make real-time improvements.
- Open-Ended Surveys and Reports - Use these to gather nuanced opinions. Maybe the training material is excellent, but the pace is too fast?
- Focus Groups and Observations - Conduct these with a cross-section of employees to get richer insights into the learning experience, identifying areas for improvement.
- Suggestion Box - A suggestion box allows employees to provide candid feedback and innovative ideas for program improvement.
A Marriage of Metrics and Mindsets
Combining quantitative data with qualitative insights will not only paint a comprehensive picture of your program's effectiveness but will also guide data-informed decisions for future improvements. For instance, if your quantitative data indicates high knowledge retention but qualitative feedback points to low engagement, you may need to inject more interactive elements into your program. Because when it comes to cybersecurity, an empowered workforce is your best line of defense.
And if you haven't already, check out NIST Special Publication 800-50 and look for the upcoming Rev. 1. This is a comprehensive guideline that serves as an invaluable resource for information security education, training, and awareness. Thank you to NIST and the industry authors and contributors for your tireless work in advancing the field and providing a foundational resource for cybersecurity professionals everywhere.
Monday, July 24, 2023
2023 PCI DSSv4 to NIST 800-53r5
I ran across
this again today working on an internal project for VMware. We are a team of
likeminded professionals who enjoy quality work and sharing with the community
to raise the bar for everyone.
What struck me
when I reopened this workbook is remembering the many very, *very* long days.
Mapping is an incomplete science, filled with subjective relationships.
However, starting from scratch, using homegrown tools and my own reading
through the controls, I remapped as accurately as I could the relationship
between the PCI DSS and the body of controls established by NIST SP 800-53r5.
We have our own
internal agendas and projects related to this work. However, the data here can
help someone else struggling with the volume of frameworks and managing the
complex relationships between all of them.
I stand by the
mapping as 90% correct. I've learned through the years there are usually ways
to improve the accuracy of subjective data. Please let me know if you find an
error! Use as you see fit. Look for 2023 PCI DSSv4 to NIST 800-53r5 on davischr2/Cloud-Documents
(github.com) or Blog Downloads (compliancequickstart.com).
#pci #pcicompliance
#nist #sp80053r5
Cross Posted on LinkedIn: PCI DSS to SP 800-53r5 | LinkedIn
Friday, July 21, 2023
NIST Privacy Framework Maturity Model
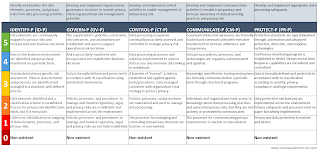
This important distinction can help drive interest and stakeholder involvement.
The implementation of any model or checklist is only useful as a point in time assessment, and finding a way to extrapolate quantifiable growth is the key to successful implementation and gaining value from the effort.
And so - along those lines - please enjoy access to a free tool for measuring your privacy framework as it stands currently versus your desired state during the next periodic timetable you choose to set.
It's unlocked. Use as you see fit: Blog Downloads (compliancequickstart.com) or davischr2/Cloud-Documents (github.com)
Cross posted on LinkedIn: NIST Privacy Framework Maturity Model | LinkedIn
Friday, July 7, 2023
Interconnected Disciplines: Security | Compliance | Privacy | Audit | Information Governance
- Security is about fortifying the enterprise against threats and ensuring the confidentiality, integrity, and availability of its data.
- Compliance takes charge of ensuring the organization's adherence to relevant laws and regulations.
- Privacy manages personal data responsibly, safeguarding the rights and expectations of the individual.
- Audit plays a vital role in conducting systematic reviews of the company's records and operations to ensure transparency and adherence to established protocols.
- Information Governance manages information at a strategic level, providing a framework that aligns data handling processes with the overarching goals of the enterprise.
Let's dive a little bit deeper into each one of these.
Criticality of Working Together
Wednesday, June 14, 2023
SOC Trust Services Criteria (TSC) AICPA Excel Spreadsheet Workbook
You can find the result under Blog Downloads (compliancequickstart.com).
Wednesday, May 31, 2023
Updated Format to New FedRAMP® NIST SP 800-53r5 Controls Workbook
Monday, May 15, 2023
Interest Profilers
I've found a profession that fits my personality and passions, and I'm equally passionate about helping others find their own personal fit. I'm watching those close to me grow up and think about the work force in the looming years with some anticipation - and some anxiety.
Interest profilers are simply a tool that can be used to help identify professions that could be a good fit based on your authentic self.
This is a list I'll update over time for my own friends and family investigating career choices.
Tuesday, February 7, 2023
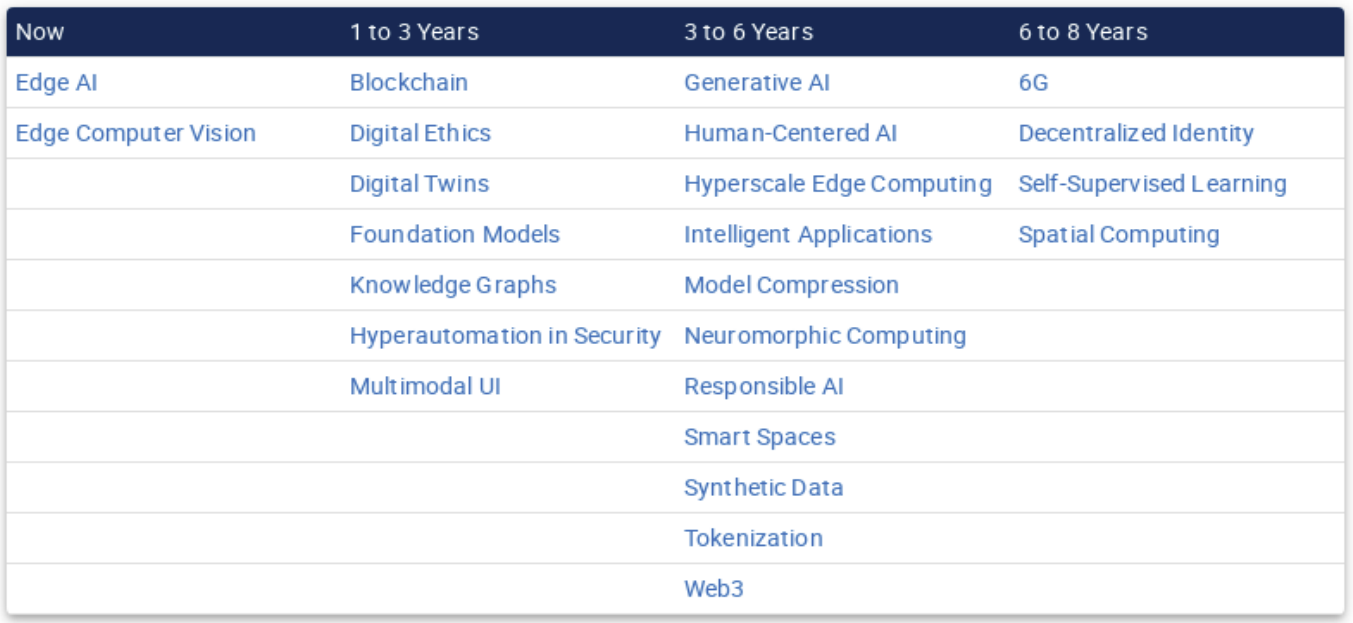
Impact Radar for 2023

This particular paper is targeted towards particle leaders to help them understand how emerging technologies and trends are changing. Staying on top of emerging technologies is necessary to decide which technologies or trends are most beneficial for their business, and when it is the right time to invest in them in order to improve their products and services.
Never lose sight of that fine line between embedded truth and the need for change. Never lose focus of the opportunities that can make you successful.
In this case, the authors created a simple chart depicting which technologies require focus now, and which ones they believe are imminent. Paying attention to these shifts helps to ensure relevance and longevity.
Thursday, January 19, 2023
Thursday, January 5, 2023
Cloud Tech Sales: Emotional Intelligence and Emotional Influence
Think of emotional intelligence as empathy and understanding the emotional state of others and how to navigate the emotions. Awareness. Think of emotional influence as deftly using this information to your advantage. Emotional influence then becomes a powerful marketing technique that aims to persuade potential customers by appealing to their emotions rather than logical arguments. When it comes to selling cloud computing technologies, some common emotions that can be appealed to include:
- Security:
Many people are concerned about the security of their data and the risk of
cyber attacks. By highlighting the robust security measures in place for
cloud computing technologies, you can appeal to people's desire for peace
of mind and protection.
- Convenience:
Cloud computing technologies offer convenience by allowing users to access
their data and applications from anywhere, at any time. By emphasizing
this convenience, you can appeal to people's desire for flexibility and
ease of use.
- Cost-effectiveness:
For businesses, moving to the cloud can be a cost-effective way to reduce
IT costs and improve efficiency. By highlighting these cost savings, you
can appeal to people's desire to save money and be financially
responsible.
- Innovation:
Cloud computing technologies can enable businesses to be more agile and
innovative by providing access to the latest technologies and enabling
them to scale quickly. By emphasizing the potential for innovation, you
can appeal to people's desire to be at the cutting edge and stay ahead of
the competition.
My wife and I became enthralled with the artful selling on a recent trip. She quickly googled to find an excellent article written by Jillian Ilao found on fitssmallbusiness.com titled "6 Emotional Selling Techniques to Drive Buying Decisions"
Jillian powerfully concludes with this:
How Effective is Emotional Selling & What are its Benefits?
Emotional selling is very effective in terms of revenue generation. Therefore, as part of your sales management process, you must train new sales reps on the emotion-based sales tactics most effective and appropriate for your products or services.
Some 70% of customers are likely to buy a product when an advertisement appeals to their emotions. They are also more likely to recommend brands they feel connected to, with 71% of customers recommending a brand based on emotional connection. Furthermore, brand loyalty also increases as 81% of emotionally engaged consumers say they enjoy giving back to a brand they are loyal to.
Wednesday, January 4, 2023
The importance of firmware security in cloud computing
One of the main risks of insecure firmware is the potential for attackers to gain unauthorized access to a system. For example, an attacker could exploit a vulnerability in the firmware to gain access to a device's network, allowing them to intercept data or launch further attacks. Insecure firmware can also make it easier for attackers to plant malware or backdoors, which can be used to maintain ongoing access to a system.
Firmware security is also important because firmware updates can introduce new vulnerabilities. If an organization fails to properly test and validate firmware updates, they may be introducing new vulnerabilities into their systems. This is particularly problematic in cloud computing environments, where multiple tenants may be sharing the same hardware.
To address these risks, it is important for organizations to implement robust firmware security measures. This can include performing regular security assessments to identify vulnerabilities, implementing robust change management processes for firmware updates, and implementing safeguards to prevent unauthorized access to firmware.
In addition to these measures, organizations should also consider using secure boot and trusted platform module (TPM) technologies to help ensure the integrity of their firmware. Secure boot helps to prevent unauthorized software from being run on a device, while TPM allows for the secure storage of cryptographic keys and other sensitive information.
The evolution of the Lockheed Martin kill chain
The Lockheed Martin Kill Chain has evolved over time as the tactics and technologies used by attackers have changed. Initially, the focus was on traditional network attacks, but the rise of mobile devices and the Internet of Things has led to the inclusion of additional stages to cover these types of attacks.
The original Lockheed Martin Kill Chain consists of seven stages:
- Reconnaissance: This is the first stage of the attack, where the attacker gathers information about the target. This may include researching the target's employees, network infrastructure, and potential vulnerabilities.
- Weaponization: In this stage, the attacker creates a means of delivering the payload (e.g., malware or exploit) to the target.
- Delivery: The payload is delivered to the target, usually via email or a malicious website.
- Exploitation: The payload is executed, allowing the attacker to gain access to the target's system.
- Installation: In this stage, the attacker installs any necessary tools or malware on the target's system to maintain control and access.
- Command and control: The attacker establishes a means of communicating with the compromised system and issuing commands.
- Actions on objectives: The attacker carries out their intended objectives, such as stealing data or disrupting services.
In addition to the seven core stages, the Lockheed Martin Kill Chain model also includes three additional stages that can occur before or after the core stages:
- Pre-attack: This stage includes activities such as supply chain attacks or the insertion of hardware backdoors.
- Post-attack: This stage includes activities such as data exfiltration and the destruction of evidence.
- Reroute: This stage includes activities such as redirecting the attack to a different target or disrupting the kill chain.
The Lockheed Martin Kill Chain model is a valuable tool for understanding the different stages of a cyber attack and for identifying potential points of intervention. By understanding the different stages of the attack, organizations can implement targeted defenses and responses to mitigate the risk of a successful attack.
Tuesday, January 3, 2023
21 skills that will pay you forever
This was shared with me. Posting so that I remember this and share with others.
21 skills that will pay you forever
1. Ability to sell and negotiate.2. Ability to convey what you think and feel.
3. Ability to break a process down into smaller steps.
4. Ability to shut up, listen and learn from others.
5. Ability to adapt, improvise and overcome obstacles.
6. Ability to read, understand and memorize.
7. Ability to walk away.
8. Ability to manage time effectively.
9. Ability to stay positive and optimistic.
10. Ability to make decisions based on facts not based on emotions.
11. Ability to speak in front of large audience.
12. Ability to keep trying even after failure.
13. Ability to invest money on yourself.
14. Ability to take action regardless of your situation.
15. Ability to self-analysis.
16. Ability to learn how to learn.
17. Ability to understand what others feel.
18. Ability to remain consistent.
19. Ability to master your thoughts.
20. Ability to write words to persuade and influence others.
21. Ability to ask for help.