Tags: SOC, XDR, Gartner, Ponemon Institute
Sources:
- XDR:
A Blessing for SOC Teams, or Another Fad? (opencybersecurityalliance.org)
- 5
observations about XDR | CSO Online
- [Gartner
Report] Innovation Insight for Extended Detection and Response
(fireeye.com)
- [Solution Page] What is
Extended Detection and Response (XDR)? | Mandiant | FireEye
- [ESG eBook] The Impact
of XDR in the Modern SOC
- [Ponemon Institute
Second Annual Study] Economics Of The SOC 2021
Relevance: What is XDR going to be when it matures? EDR… XDR… It's not quite the same thing. XDR is starting to gain traction as a beloved moniker. How do we shape the industry and VMware's story? The following is a representative, but not exhaustive, list of potential future XDR vendors from Gartner’s Innovation Insight: Cisco, Fortinet, Fidelis Cybersecurity, McAfee, Microsoft, Palo Alto Networks, Symantec, Trend Micro, FireEye, Rapid7, and Sophos. How does VMware fit into this narrative?
Pushing this further – welcome to the intersection of XDR and the SOC.
From Gartner Innovation Insight report:
The three primary requirements of
an XDR system are:
1.
Centralization of normalized data, but primarily
focusing on the XDR vendors’ ecosystem only.
2.
Correlation of security data and alerts
into incidents.
3. A centralized incident response capability that can change the state of individual security products as part of incident response or security policy setting.
Extended Detection and
Response Conceptual Architecture:
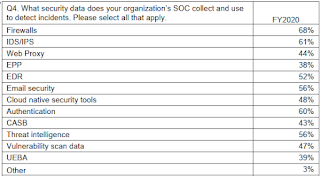
This was insightful from the Ponemon Institute research
report on SOCs: