Sometimes a picture says it all!
This blog is about understanding, auditing, and addressing risk in cloud environments. Systems and architectures are rapidly converging, hiding complexity with additional layers of abstraction. Simplicity is great for operations - as long as risks are understood and appropriately addressed.
Thursday, October 3, 2024
Wednesday, September 25, 2024
Prioritizing Vulnerabilities
Here are a few quick thoughts on prioritization everyone should know.
A respected peer was discussing the use of EPSS to add detail into the decision-making process for what’s relevant and should be a focus.
What does this mean? Why do you care?
Here’s a practical application for prioritizing if you have a CVSS associated with a finding. The CVSS provides the base score. Let's assume a quick scoring adjustment review, and great – it doesn’t look too bad. However, you see the associated vulnerability on the KEV and in the EPSS data (used by AWS, Wiz, and many others to add color to their findings) with a high percentage.
Stop. Consider. Maybe that particular finding should be prioritized higher. Take the information in as input. It's a data point. It's not the authority - your organization is the authority - but consider the additional information as something to consider.
Here are some links. Remember this table. This information will be helpful at some point.
|
Scoring
System |
Link |
Scoring
Range |
Purpose |
|
NVD - Vulnerability Metrics (NIST) |
0.0 - 10.0 (CVSS) |
Provides severity ratings for vulnerabilities based on the
Common Vulnerability Scoring System (CVSS) to guide remediation efforts. |
|
|
Known Exploited Vulnerabilities Catalog (CISA) |
Binary (Exploited/Not Exploited) |
A list of vulnerabilities that are known to be actively
exploited in the wild, maintained to help prioritize patching. |
|
|
Exploit Prediction Scoring System (EPSS) |
0 - 1 (0% to 100% likelihood) |
Predicts the likelihood of a vulnerability being exploited
in the next 30 days, helping organizations prioritize remediation. |
Tuesday, August 27, 2024
Requirements for FIPS Validated Modules
The following are common sets of requirements for FIPS validated modules.
Do you need them? Depends. This is certainly compelling.
PCI DSSv4
Payment
Card Industry Data Security Standard (pcisecuritystandards.org) [Page 70]
These and other non-console access
technologies and methods must be secured with strong cryptography. Further
Information Refer to industry standards and best practices such as NIST SP
800-52 and SP 800-57.
Privacy – PII & the GSA
Rules
and Policies - Protecting PII - Privacy Act | GSA
Rules and Policies - Protecting PII
- Privacy Act. The term “PII,” as defined in OMB Memorandum M-07-1616 refers to
information that can be used to distinguish or trace an individual’s identity,
either alone or when combined with other personal or identifying information
that is linked or linkable to a specific individual.
Protecting PII. PII shall be
protected in accordance with GSA
Information Technology (IT) Security Policy, Chapter 4.
8. NIST SP (800 Series) and GSA guidance documents. All policies shall be implemented using the appropriate special publication from NIST and/or GSA procedural guides to the greatest extent possible. […] Federal Information Processing Standards (FIPS) publication requirements are mandatory for use at GSA. [Page 6]
NIST SP 800-52
Abstract
Transport Layer Security (TLS)
provides mechanisms to protect data during electronic dissemination across the
Internet. This Special Publication provides guidance to the selection and
configuration of TLS protocol implementations while making effective use
of Federal Information Processing Standards (FIPS) and NIST-recommended
cryptographic algorithms. It requires that TLS 1.2 configured
with FIPS-based cipher suites be supported by all government TLS servers and
clients and requires support for TLS 1.3 by January 1, 2024.
NIST SP 800-57
Recommendation
for Key Management: Part 1 - General (nist.gov) [Page 3-4]
1.4 Purpose of FIPS and
NIST Recommendations (NIST Standards) Federal Information Processing
Standards (FIPS) and NIST Recommendations, collectively referred to as “NIST
standards,” are valuable because:
1.
They establish an acceptable minimal level of
security for U.S. government systems. Systems that implement these NIST
standards offer a consistent level of security that is approved for the
protection of sensitive, unclassified government information.
2.
They often establish some level of
interoperability between different systems that implement the NIST standards.
For example, two products that both implement the Advanced Encryption Standard
(AES)10 cryptographic algorithm have the potential to interoperate, provided
that the other functions of the product are compatible.
3.
They often provide for scalability because the
U.S. government requires products and techniques that can be effectively
applied in large numbers.
4.
They are scrutinized by U.S. government experts
and the public to ensure that they provide a high level of security. The NIST
standards process invites broad public participation, not only through the
formal NIST public review process before adoption but also by interaction with
the open cryptographic community through NIST workshops, participation in
voluntary standards development organizations, participation in cryptographic
research conferences, and informal contacts with researchers. NIST encourages
the study and cryptanalysis of NIST standards. Inputs on their security are
welcome at any point, including during the creation of the initial
requirements, during development, and after adoption.
5.
NIST-approved cryptographic techniques are
periodically reassessed for their continued effectiveness. If any technique is
found to be inadequate for the continued protection of government information,
the NIST standard is revised or discontinued.
6.
The algorithms specified in NIST standards
(e.g., AES, SHA-2, and ECDSA) and the cryptographic modules in which they
reside have required conformance tests. Accredited laboratories perform these
tests on vendor implementations that claim conformance to the standards.
Vendors are required to modify nonconforming implementations so that they meet
all applicable requirements. Users of validated implementations can have a high
degree of confidence that validated implementations conform to the standards.
Since 1977, NIST has developed a
cryptographic “toolkit” of NIST standards that form a basis for the
implementation of approved cryptography. This Recommendation references many of
those standards and provides guidance on how they may be properly used to
protect sensitive information.
CUI [NIST SP 800-171]
Protecting
Controlled Unclassified Information in Nonfederal Systems (nist.gov) [Page
14, see 3.1.13]
3.1.13 Employ cryptographic
mechanisms to protect the confidentiality of remote access sessions. DISCUSSION
Cryptographic standards include FIPS-validated cryptography and NSA-approved
cryptography. See [NIST CRYPTO]; [NIST CAVP]; [NIST CMVP]; National Security
Agency Cryptographic Standards.
AC-17(2) Remote Access Protection
of Confidentiality / Integrity Using Encryption
HIPAA [NIST SP 800-66]
NIST
SP 800-66r2 initial public draft, Implementing the Health Insurance Portability
and Accountability Act (HIPAA) Security Rule: A Cybersecurity Resource Guide
[Pages 121, 123, and 135]
164.312(e)(1) Transmission
Security: Implement technical security measures to guard against unauthorized
access to electronic protected health information that is being transmitted
over an electronic communications network.
Guidelines for the Selection,
Configuration, and Use of Transport Layer Security 1852 (TLS) Implementations
[SP 800-52] – Provides guidance on the selection and configuration of TLS
protocol implementations while making effective use of Federal Information
Processing Standards (FIPS) and NIST-recommended cryptographic algorithms.
CMMC
CMMC
Assessment Guide - Level 2 (osd.mil) [Page 229]
SC.L2-3.13.11 – CUI ENCRYPTION
FIPS-validated cryptography means
the cryptographic module has to have been tested and validated to meet FIPS
140-1 or-2 requirements. Simply using an approved algorithm is not sufficient –
the module (software and/or hardware) used to implement the algorithm must be
separately validated under FIPS 140. Accordingly, FIPS-validated
cryptography is required to meet CMMC practices that protect CUI when
transmitted or stored outside the protected environment of the covered
contractor information system (including wireless/remote access). Encryption
used for other purposes, such as within applications or devices within the
protected environment of the covered contractor information system, would not
need to be FIPS-validated.
This practice, SC.L2-3.13.11,
complements AC.L2-3.1.19, MP.L2-3.8.6, SC.L2-3.13.8, and SC.L2-3.13.16 by
specifying that FIPS-validated cryptography must be used.
Tuesday, August 13, 2024
NIST Releases First 3 Finalized Post-Quantum Encryption Standards
NIST has finalized three post-quantum encryption standards designed to protect electronic information from future quantum computer attacks. These include ML-KEM for general encryption, ML-DSA for digital signatures, and SLH-DSA as a backup digital signature algorithm. These standards are part of NIST's broader effort to secure data against quantum threats, encouraging immediate adoption by system administrators.
A fourth algorithm, FN-DSA, is scheduled for release in late 2024. This initiative is part of a decade-long project to develop quantum-resistant cryptography.
Friday, August 9, 2024
Increasing the Work Factor: Enhancing Security to Deter Attackers
In the constantly evolving landscape of cybersecurity, defending your systems against attackers requires more than just strong passwords and firewalls. One of the most effective strategies you can employ is to increase the "work factor"—a term that refers to the amount of effort, time, and resources an attacker must expend to compromise a system. By increasing the work factor, you can make your system less attractive to attackers, ultimately forcing them to abandon their efforts and seek out easier targets.
In this post, we'll explore several methods to increase
the work factor and discuss how they can be implemented to strengthen your
system's defenses.
1. Implement Timeout Mechanisms
Timeouts are a simple yet powerful way to increase
the work factor for attackers. When a user (or attacker) enters incorrect
credentials multiple times, the system can implement a timeout, delaying
further attempts for a certain period. This prevents attackers from quickly
cycling through password attempts (brute force attacks) and forces them to slow
down.
Implementation:
•
Login Attempt Timeouts: After a set
number of failed login attempts, impose a delay before allowing further
attempts. For example, after 5 incorrect attempts, impose a 30-second delay.
•
Session Timeouts: Automatically log out
users after a period of inactivity, forcing attackers to restart their efforts
if they gain access to an idle session.
2. Enforce Quota and Rate Limits
Quota and rate limits are another effective way to
increase the work factor. These limits restrict the number of actions that can
be performed in a given time period, making it harder for attackers to execute
automated attacks.
Implementation:
•
API Rate Limiting: Set limits on the
number of API requests that can be made within a certain timeframe. For
example, allow only 100 requests per minute per IP address. This thwarts
attackers who use automated scripts to bombard your system with requests.
•
Password Reset Limits: Limit the number
of password reset requests that can be made in a specific timeframe. This
prevents attackers from abusing the password reset functionality to lock out
legitimate users or gain access to accounts.
3. Use CAPTCHA and Other Human Verification Methods
Adding CAPTCHA challenges or other human verification
methods is a proven way to increase the work factor by ensuring that only human
users (not bots) can interact with your system. This is especially useful for
login forms, registration forms, and other areas where automated attacks are
common.
Implementation:
•
Login CAPTCHAs: Implement a CAPTCHA
challenge after a certain number of failed login attempts or on every login
attempt. This makes it significantly harder for automated scripts to continue
brute-forcing passwords.
•
Registration CAPTCHAs: Require CAPTCHA
completion during user registration to prevent bots from creating fake
accounts.
4. Apply Progressive Delays and Exponential Backoff
Progressive delays and exponential backoff
increase the time between allowed attempts as the number of failed attempts
grows. This strategy greatly increases the work factor by making each
successive attempt take longer than the last, discouraging persistent
attackers.
Implementation:
•
Login Backoff: After each failed login
attempt, increase the delay before the next attempt is allowed. For example,
after 3 failed attempts, wait 10 seconds, after 4, wait 30 seconds, and so on.
•
API Call Backoff: For API requests,
implement exponential backoff on rate limits, gradually increasing the wait
time between requests after each limit breach.
5. Introduce Account Lockout Mechanisms
Account lockouts can be a strong deterrent against
brute force attacks by locking an account after a certain number of failed
login attempts. While this method needs careful implementation to avoid
denial-of-service attacks against legitimate users, it can significantly
increase the work factor for attackers.
Implementation:
•
Temporary Lockouts: After a defined
number of failed login attempts, temporarily lock the account for a period
(e.g., 15 minutes). Notify the user of the lockout and provide instructions for
regaining access.
•
Permanent Lockouts with Administrator
Intervention: For more critical systems, consider locking accounts
permanently after multiple failed attempts, requiring manual intervention by an
administrator to unlock them.
6. Implement Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) adds an additional
layer of security by requiring users to provide multiple forms of verification
(e.g., a password and a one-time code sent to their phone). This drastically
increases the work factor for attackers, as they must compromise more than just
the user’s password.
Implementation:
•
Mandatory MFA: Make MFA mandatory for all
users, especially for accessing sensitive systems or performing critical
actions like changing account details or making financial transactions.
•
Adaptive MFA: Use adaptive MFA, which
requires additional verification only when the system detects unusual behavior,
such as login attempts from a new device or location.
Focus on the Strategic Outcome
Increasing the work factor for attackers is a strategic
approach to improving your system's security. By implementing timeouts, quota
thresholds, human verification methods, and other limits, you can make it
significantly more difficult for attackers to successfully compromise your
system. These measures, while simple, can have a profound impact on the
security of your systems by making them less attractive targets for
cybercriminals. By applying these strategies, you’re not only protecting your
resources but also sending a clear message: attacking your system is simply not
worth the effort.
Remember, the goal is to make the attacker's job so
laborious and time-consuming that they abandon their efforts and move on to
easier prey.
Friday, August 2, 2024
Threat Model: CREATE
This was an interesting experiment working with two different chat models and focusing on the "often-emphasized" strengths of each threat model method. This isn't an exact science - nor is it intended to be an exact science. But I liked the result.
CREATE stands for Comprehensive Risk Evaluation and
Threat Elimination. This acronym encapsulates the integrated approach of
visualizing system architecture, identifying threats, measuring impact,
addressing privacy concerns, and determining effective countermeasures.
CREATE Threat Model Steps
- Comprehend the System (Visualize - VAST)
- Develop a high-level architecture diagram of the system, focusing on key components, data flows, and trust boundaries.
- Ensure the diagram is simple, visual, and easy to understand for all stakeholders.
- Identify potential threat actors who may have a vested interest in attacking the system.
- Recognize Assets and Threats (Threats - STRIDE)
- Identify and prioritize critical assets that require protection.
- Break down the application into smaller, manageable components and identify trust boundaries and interactions between the components.
- Identify potential threats for each component and interaction using the STRIDE model:
- Spoofing: Identify threats related to authentication and impersonation.
- Tampering: Identify threats related to unauthorized modification of data or systems.
- Repudiation: Identify threats related to the ability to deny actions or transactions.
- Information Disclosure: Identify threats related to the unauthorized exposure of sensitive data.
- Denial of Service: Identify threats related to the disruption or degradation of system availability.
- Elevation of Privilege: Identify threats related to gaining unauthorized access or permissions.
- Evaluate Risks (Impact - DREAD)
- Assess the likelihood and potential impact of each identified threat using the DREAD model:
- Damage: Assess the potential damage caused by the threat if it were to occur.
- Reproducibility: Determine how easily the threat can be reproduced or exploited.
- Exploitability: Evaluate the level of skill and resources required to exploit the threat.
- Affected Users: Assess the number of users or systems that could be impacted by the threat.
- Discoverability: Determine how easily the vulnerability or weakness can be discovered by potential attackers.
- Address Privacy Concerns (Privacy - LINDDUN)
- Identify potential privacy threats using the LINDDUN model:
- Linkability: Determine if data from different sources can be combined to identify an individual or link their activities.
- Identifiability: Assess if an individual can be singled out or identified within a dataset.
- Non-repudiation: Evaluate if an individual can deny having performed an action or transaction.
- Detectability: Determine if it is possible to detect that an item of interest exists within a system.
- Disclosure of Information: Assess the risk of unauthorized access to or disclosure of sensitive information.
- Unawareness: Evaluate if individuals are unaware of the data collection, processing, or sharing practices.
- Non-compliance: Determine if the system or practices are not compliant with privacy laws, regulations, or policies.
- Terminate Threats (Countermeasures - PASTA)
- Create and review attack models using the PASTA methodology to:
- Define Objectives: Establish the objectives and scope of the attack modeling exercise.
- Define Technical Scope: Identify the key components, data flows, and trust boundaries of the system.
- Application Decomposition: Break down the application into smaller, manageable components.
- Threat Analysis: Identify and analyze potential threats using attack trees, threat intelligence, and vulnerability data.
- Vulnerability & Weaknesses Analysis: Assess the system for vulnerabilities and weaknesses that could be exploited.
- Attack Modeling: Simulate potential attack scenarios to determine the likelihood and impact of each threat.
- Risk & Impact Analysis: Evaluate the risk and potential impact of each identified threat.
- Countermeasure Analysis: Develop and recommend countermeasures to mitigate the identified risks.
CREATE Summary
- Comprehend the System: Visualize the system architecture and identify threat actors.
- Recognize Assets and Threats: Identify and categorize potential threats to the system.
- Evaluate Risks: Measure and prioritize the impact and likelihood of identified threats.
- Address Privacy Concerns: Review privacy-specific concerns within the threat model.
- Terminate Threats: Evaluate data and determine effective countermeasures.
The CREATE model provides an integrated approach to threat modeling by combining the
strengths of VAST, STRIDE, DREAD, LINDDUN, and PASTA into a unified framework.
Wednesday, July 17, 2024
Systems Security Engineering Design Principles: One-liners...
I'm sharing a concise list of security design principles extracted from NIST Special Publication 800-160 on System Security Engineering. Each principle is accompanied by a brief, one-line definition to provide readers with a quick understanding of key concepts in secure system design. This resource is intended to serve as a handy reference for professionals and students in the field of cybersecurity and system engineering.
- Security Architecture and Design: The structured framework that
defines the security controls and measures to protect systems and data.
- Clear Abstraction: Simplifying complex systems into understandable and
manageable components to enhance security.
- Hierarchical Trust: Establishing trust levels in a layered manner, where
higher levels inherit trust from lower levels.
- Least Common Mechanism: Minimizing shared resources among
users to reduce the risk of unauthorized access.
- Inverse Modification Threshold: Ensuring that the more critical a
system component is, the less frequently it should be modified.
- Modularity and Layering: Designing systems in discrete
modules and layers to isolate and protect components.
- Hierarchical Protection: Implementing security controls in a
tiered manner to provide multiple layers of defense.
- Partially Ordered Dependencies: Managing dependencies in a way that
some components can operate independently to enhance security.
- Minimized Security Elements: Reducing the number of security
mechanisms to simplify management and reduce potential vulnerabilities.
- Efficiently Mediated Access: Ensuring that access controls are
both effective and efficient to prevent unauthorized access without hindering
performance.
- Least Privilege: Granting users the minimum level of access necessary to perform their
functions.
- Minimized Sharing: Reducing the sharing of resources among users to
limit the potential for security breaches.
- Predicate Permission: Granting permissions based on specific conditions or
predicates to enhance security.
- Reduced Complexity: Simplifying systems to make them easier to secure and
manage.
- Self-Reliant Trustworthiness: Ensuring that systems can maintain
their security integrity independently.
- Secure Evolvability: Designing systems to adapt securely to new threats
and changes over time.
- Secure Distributed Composition: Ensuring that distributed systems
maintain security across all components and interactions.
- Trusted Components: Using components that are verified and trusted to
maintain system security.
- Trusted Communication Channels: Ensuring that communication channels
are secure and trusted to prevent data breaches.
- Security Capability and Intrinsic Behaviors: Embedding security
capabilities and behaviors within systems to enhance protection.
- Continuous Protection: Implementing ongoing security measures to protect
systems and data continuously.
- Secure Failure and Recovery: Ensuring that systems fail securely
and can recover without compromising security.
- Secure Metadata Management: Protecting metadata to prevent
unauthorized access and manipulation.
- Economic Security: Balancing security measures with cost-effectiveness
to ensure sustainable protection.
- Self-Analysis: Enabling systems to analyze their own security posture and detect
vulnerabilities.
- Performance Security: Ensuring that security measures do not significantly
impact system performance.
- Accountability and Traceability: Implementing mechanisms to track and
hold users accountable for their actions.
- Human Factored Security: Designing security measures that
consider human behavior and usability.
- Secure Defaults: Configuring systems with secure default settings to enhance protection
from the start.
- Acceptable Security: Ensuring that security measures meet the required
standards and are acceptable to stakeholders.
- Life Cycle Security: Implementing security measures throughout the entire
lifecycle of a system or product.
- Repeatable and Documented Procedures: Establishing and documenting
security procedures to ensure consistency and reliability.
- Secure System Modification: Ensuring that system modifications
are performed securely to prevent introducing vulnerabilities.
- Procedural Rigor: Applying strict and thorough procedures to maintain
high security standards.
- Sufficient Documentation: Providing comprehensive
documentation to support security measures and procedures.
Friday, March 15, 2024
Integrated Threat Modeling: VAST, STRIDE, DREAD, LINDDUN, and PASTA
Recently, during an Interview, I was asked about threat modeling. I've been in and around threat modeling for a few decades, identifying and prioritizing risks based on quantitative and qualitative data. It's germane to the principles of Information Security, Assurance, and Trust. The different shifting focus areas over time may require updated approaches, but the objective remains. Find and prioritize threats for risk mitigation based on our risk threshold prior to an exposure.
Towards that end - I thought it'd be interesting to engage Claude's Opus model in a conversation about a few different approaches. There were several outputs I liked with a little tweaking. Below is just one example that includes VAST, STRIDE, DREAD, LINDDUN, and PASTA.
Now - Carefully - The output below has some duplicity and can be further refined - a lot - for efficient workflow execution. This demonstrates the overlap and use of each of these models.
Example Integrated Threat Modeling Process:
Define Objectives and Scope:
- Establish the goals and objectives of the threat modeling exercise.
- Determine the scope of the assessment, including the systems, applications, and business units involved.
Identify Assets:
- Identify the critical assets within the defined scope that require protection.
- Prioritize the assets based on their value and importance to the organization.
Create Architecture Overview. This incorporates the core principle of the VAST model (Visual, Agile, Simple Threat modeling):
- Develop a high-level architecture diagram of the system, focusing on key components, data flows, and trust boundaries.
- Ensure the diagram is simple, visual, and easy to understand for all stakeholders.
Identify Threat Actors:
- Identify potential threat actors who may have a vested interest in attacking the system.
- Consider both internal and external threat actors, such as malicious insiders, cybercriminals, nation-state actors, and competitors.
- Assess the motivations, capabilities, and resources of each threat actor.
Decompose Application and Identify Threats:
- Break down the application into smaller, manageable components and identify trust boundaries and interactions between the components.
- Identify potential threats for each component and interaction using the STRIDE model (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) to:
- Spoofing: Identify threats related to authentication and impersonation.
- Tampering: Identify threats related to unauthorized modification of data or systems.
- Repudiation: Identify threats related to the ability to deny actions or transactions.
- Information Disclosure: Identify threats related to the unauthorized exposure of sensitive data.
- Denial of Service: Identify threats related to the disruption or degradation of system availability.
- Elevation of Privilege: Identify threats related to gaining unauthorized access or permissions.
- Utilize attack trees, threat intelligence, and vulnerability data to assist in threat identification.
Analyze Threats and Vulnerabilities:
- Assess the likelihood and potential impact of each identified threat using the DREAD model (Damage, Reproducibility, Exploitability, Affected Users, Discoverability):
- Damage: Assess the potential damage caused by the threat if it were to occur.
- Reproducibility: Determine how easily the threat can be reproduced or exploited.
- Exploitability: Evaluate the level of skill and resources required to exploit the threat.
- Affected Users: Assess the number of users or systems that could be impacted by the threat.
- Discoverability: Determine how easily the vulnerability or weakness can be discovered by potential attackers.
- Identify potential privacy threats using the LINDDUN model (Linkability, Identifiability, Non-repudiation, Detectability, Disclosure of Information, Unawareness, Non-compliance):
- Linkability: Determine if data from different sources can be combined to identify an individual or link their activities.
- Identifiability: Assess if an individual can be singled out or identified within a dataset.
- Non-repudiation: Evaluate if an individual can deny having performed an action or transaction.
- Detectability: Determine if it is possible to detect that an item of interest exists within a system.
- Disclosure of Information: Assess the risk of unauthorized access to or disclosure of sensitive information.
- Unawareness: Evaluate if individuals are unaware of the data collection, processing, or sharing practices.
- Non-compliance: Determine if the system or practices are not compliant with privacy laws, regulations, or policies.
- Conduct vulnerability and weakness analysis using scanning tools, penetration testing, and code review techniques.
Perform Attack Modeling:
- Create and review attack models using the PASTA model (Process for Attack Simulation and Threat Analysis) methodology to:
- Define Objectives: Establish the objectives and scope of the attack modeling exercise.
- Define Technical Scope: Identify the key components, data flows, and trust boundaries of the system.
- Application Decomposition: Break down the application into smaller, manageable components.
- Threat Analysis: Identify and analyze potential threats using attack trees, threat intelligence, and vulnerability data.
- Vulnerability & Weaknesses Analysis: Assess the system for vulnerabilities and weaknesses that could be exploited.
- Attack Modeling: Simulate potential attack scenarios to determine the likelihood and impact of each threat.
- Risk & Impact Analysis: Evaluate the risk and potential impact of each identified threat.
- Countermeasure Analysis: Develop and recommend countermeasures to mitigate the identified risks.
- Analyze the feasibility of each attack scenario.
Evaluate Risk and Impact:
- Assess the overall risk posture of the system based on the identified threats, vulnerabilities, and attack models.
- Determine the potential impact of each risk on the organization's business objectives and operations.
Decide on Countermeasures:
- Develop and recommend countermeasures to mitigate the identified risks.
- Consider the effectiveness, feasibility, and cost of each countermeasure.
- Prioritize the implementation of countermeasures based on the risk level and available resources.
Validate and Iterate:
- Review the threat model with stakeholders and subject matter experts.
- Validate the assumptions made during the modeling process and update the model as necessary.
- Iterate the threat modeling process regularly to account for changes in the system, new threats, and emerging vulnerabilities.
Communicate and Educate:
- Communicate the results of the threat modeling exercise to relevant stakeholders, including management, development teams, and security personnel.
- Provide training and awareness sessions to ensure that all stakeholders understand their roles and responsibilities in mitigating the identified risks.
Implement and Monitor:
- Implement the selected countermeasures and integrate them into the system development lifecycle.
- Establish monitoring and logging mechanisms to detect and respond to potential security incidents.
- Regularly review and update the threat model and countermeasures based on changes in the system and the evolving threat landscape.
AI Revolution: Smarter Development, Stronger Security
The cloud computing landscape is experiencing a seismic shift driven by the exponential integration of Artificial Intelligence (AI). Recent advancements like Cognition AI's Devin and Microsoft's Copilot for Security showcase AI's potential to revolutionize software development and cybersecurity.
Pay attention to the oncoming freight train of changes quickly coming to the computing world.
Examples include:
- AI Agents working in teams: Effectively. Perfect? No. Getting better? Quickly. E.g. Cognition AI's Devin
- Topically Focused LLMs, LAMs, etc.: E.g. Microsoft's Copilot for Security. Or any topic you can think about. I developed one to teach social skills to a teenage girl in less than an hour.
- UI Navigation: Think about how the future of natural language query looks when I don't have to be an expert on the system UI anymore.
- Happening for the last year: The knowledge barrier to entry for many tasks continue to drop. Used to be There's an app for that... Now... There's an AI for that.
AI Agents: The Realistic Future of Development
Cognition AI's Devin is a groundbreaking AI agent that plans and executes software projects with minimal human input. Operating autonomously in a sandbox environment, Devin learns from experience, rectifies mistakes, and utilizes tools like code editors and web browsers. Devin isn't meant to replace engineers, but rather augment them, freeing human talent for more complex tasks and ambitious goals.
Imagine AI agents like Devin seamlessly integrated into cloud environments. This could significantly enhance development efficiency and scalability. AI can automate routine tasks, assist in code development, optimize resource allocation, and improve system performance, all while reducing costs and development times. Furthermore, these AI collaborators can provide real-time insights, identify potential issues, and suggest improvements, fostering a truly collaborative approach to cloud-based software development.
AI-Powered Security: Every. Single. Tool.
Microsoft's Copilot for Security highlights the growing role of AI in tackling cloud security challenges. This AI-powered chatbot, leveraging OpenAI's GPT-4 and Microsoft's security expertise, assists security professionals in identifying and defending against threats. Copilot for Security will utilize the 78 trillion signals collected by Microsoft’s threat intelligence. Copilot provides real-time security updates, facilitates collaboration among teams, and even answers questions in natural language.
Integrating AI chatbots like Copilot into the cloud security landscape can significantly enhance threat detection and response. By analyzing code and files, providing real-time updates on security incidents, and enabling natural language queries, AI helps organizations stay ahead of threats and respond more effectively to cyberattacks. Additionally, AI chatbots lowers the barrier to knowledge sharing and breaks down silos, fostering a more coordinated approach to cloud cybersecurity.
Scalability, Flexibility, and the Cloud's Future
The growing demand for adaptable AI solutions is reflected in Microsoft's pay-as-you-go pricing model for Copilot for Security. As AI becomes more embedded in cloud computing, expect to see more consumption-based pricing models, making AI-powered services accessible to businesses of all sizes.
The convergence of AI and cloud computing promises to drive innovation across industries. AI-driven automation and collaboration will be cornerstones of future cloud computing, enhancing efficiency, security, and scalability. As AI agents and chatbots like Devin and Copilot evolve, we can expect a future where AI seamlessly collaborates with human professionals, unlocking new opportunities for success in the cloud era.
Embracing the Future: Be prepared. Be proactive.
The introduction of Devin and Copilot for Security exemplifies AI's transformative impact on cloud-based development and security. By embracing AI-driven automation and collaboration, cloud providers and organizations can position themselves at the forefront of this revolution, driving innovation, efficiency, and security. As AI continues to shape the future of cloud computing, businesses that adapt and harness these technologies will be best equipped. Be prepared. Be proactive.
Tuesday, March 12, 2024
Staying Current - Relevant - Continuous Learning
Protect your organization. Cybersecurity is a dynamic field where new threats, vulnerabilities, and technologies change, evolve, and emerge. Commit to continuous learning and skill development. Stay informed about the latest security trends, best practices, and tools.
Resources for Staying Current:
Vendor-Specific Security Advisories:
Stay informed about security updates and patches from major technology companies.
- Microsoft Security Advisories: https://msrc.microsoft.com/update-guide
- Cisco Security Advisories: https://tools.cisco.com/security/center/publicationListing.x
- Oracle Critical Patch Updates and Security Alerts: https://www.oracle.com/security-alerts/
- Apple Security Updates: https://support.apple.com/en-us/HT201222
- Intel Security Center: https://www.intel.com/content/www/us/en/security-center/default.html
- Amazon Security Bulletins: https://aws.amazon.com/security/security-bulletins/
- Amazon Web Services (AWS) Security Bulletins: https://aws.amazon.com/security/security-bulletins/
- Alibaba Cloud Security Bulletins: https://www.alibabacloud.com/solutions/security
- Google Cloud Platform Security Bulletins: https://cloud.google.com/support/bulletins
- Microsoft Azure Security Advisories: https://learn.microsoft.com/en-us/azure/service-health/stay-informed-security
- Oracle Cloud Security Advisories: https://www.oracle.com/security-alerts/
Government and Non-Profit Security Organizations:
Follow updates from organizations for authoritative guidance and best practices.
- CISA: https://www.cisa.gov/about/contact-us/subscribe-updates-cisa
- NIST: https://www.nist.gov/cybersecurity
- US-CERT: https://www.us-cert.gov/ | https://public.govdelivery.com/accounts/USDHSCISA/subscriber/new?qsp=CODE_RED
- CVE & MITRE: https://www.cve.org, https://cve.mitre.org
Cybersecurity News and Blogs:
Stay informed about the latest security incidents, trends, and analysis through popular blogs and news sites.
- Krebs on Security: https://krebsonsecurity.com/
- DarkReading: https://www.darkreading.com/
- SecurityWeek: https://www.securityweek.com/
- The Register: https://www.theregister.com/security/
- The Hacker News: https://thehackernews.com/
- CSO Online: https://www.csoonline.com/
- Threat Post: https://threatpost.com/
- Graham Cluley: https://www.grahamcluley.com/
Security Mailing Lists & Vulnerability Databases:
Subscribe to mailing lists to receive timely information about new vulnerabilities and exploits. You can do this to regularly check vulnerability databases to stay informed about newly discovered vulnerabilities and their potential impact.
- Full Disclosure: http://seclists.org/fulldisclosure/
- National Vulnerability Database (NVD): https://nvd.nist.gov/general/email-list
- Exploit-DB: https://www.exploit-db.com/
- Openwall: https://www.openwall.com/lists/
Security Conferences:
Attend conferences to learn from industry experts, network with peers, and stay updated on the latest research and trends. Also check out the YouTube channels for each of these to see what talks have been recently published.
- BlackHat: https://www.blackhat.com/
- DEF CON: https://defcon.org/
- RSA Conference: https://www.rsaconference.com/
- SANS Institute Cyber Security Conferences: https://www.sans.org/cyber-security-training-events/
- Infosecurity Europe: https://www.infosecurityeurope.com/
- BSides (Various locations): http://www.securitybsides.com/
Online Security Communities:
Engage with online communities to learn from others, ask questions, and contribute to discussions.
- Reddit r/netsec: https://www.reddit.com/r/netsec/
- Reddit r/cybersecurity: https://www.reddit.com/r/cybersecurity/
- Information Security Stack Exchange: https://security.stackexchange.com/
- SANS Internet Storm Center: https://isc.sans.edu/
- OWASP (Open Web Application Security Project): https://owasp.org/
Again, this isn't a complete, all-inclusive list of resources. Not even close. The objective is to provide exposure to options and importance. Other media I find to be helpful includes YouTube, Claude and other AI chat, and audiobooks.
Continuous learning is essential. Make the choice to stay current, relevant, and effective. Yes, it's hard sometimes. It takes intentionality - and a little goes a long way. You can do it...! There are many, many more than just these sources. The purpose is to develop a comprehensive approach to continuous learning that combines staying informed about the latest security news, following best practices, and engaging with the cybersecurity community.
Thursday, February 15, 2024
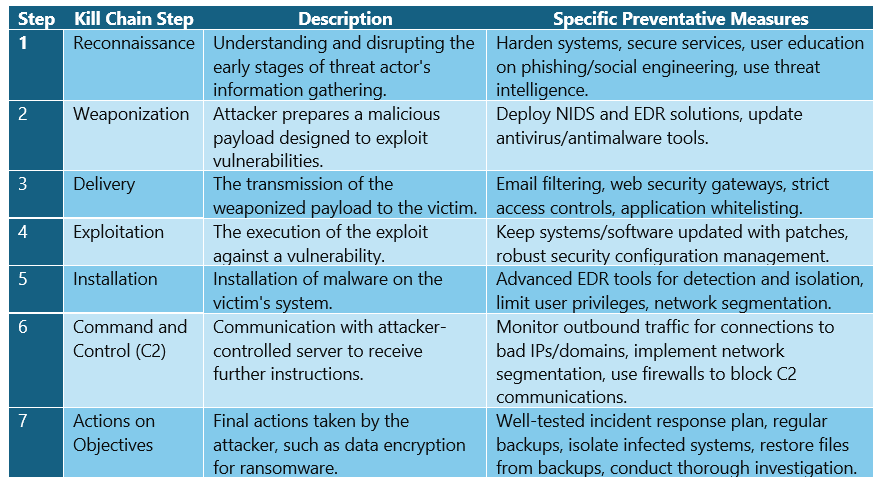
Ransomware Maturity and Kill Chains
Creating a maturity model to measure the effectiveness of remediations in preparing for and addressing common ransomware attacks involves developing a framework that assesses an organization's cybersecurity capabilities and readiness across multiple dimensions. This model typically ranges from initial (least mature) to optimized (most mature) stages, providing a path for continuous improvement. Here's how to create such a maturity model:
1. Define the Maturity Levels to be Used for Measurements (e.g.):
- Initial (Level 1): Basic processes are ad-hoc, and ransomware preparedness is minimal or non-existent.
- Developing (Level 2): Awareness of ransomware threats exists, with some informal processes and basic defensive measures in place.
- Defined (Level 3): Formal processes and policies are established, with proactive measures to prevent ransomware attacks.
- Managed (Level 4): Advanced defensive measures and continuous monitoring are in place, with a focus on managing and mitigating ransomware threats.
- Optimized (Level 5): The organization continuously improves its ransomware defense mechanisms, leveraging advanced analytics, machine learning, and threat intelligence for predictive defense.
2. Identify Key Domains for Assessment
Break down the organization's cybersecurity posture into key domains. Take a quick look at the table above and you'll see common expectations such as:
- Threat Intelligence
- Identity and Access Management
- Endpoint Protection
- Network Security
- Incident Response and Recovery
- User Training and Awareness
3. Develop Assessment Criteria for Each Domain
For each domain, define specific criteria that measure the organization's maturity. These criteria should cover the processes, technologies, and practices relevant to preventing and responding to ransomware attacks. Criteria can include the effectiveness of backup and recovery strategies, the extent of employee training programs, the implementation of EDR solutions, etc.
4. Establish Metrics and Indicators
Define quantitative and qualitative metrics for evaluating maturity in each domain. Metrics could include the frequency of security audits, the speed of patch deployment, the number of successful phishing simulations, or the recovery time after an incident.
5. Conduct Assessments
Perform regular assessments against the maturity model to determine the current level of preparedness and effectiveness of ransomware remediation efforts. This involves gathering data through audits, interviews, and technical testing.
6. Analyze Results and Identify Gaps
Analyze the assessment results to identify gaps in the organization's ransomware preparedness. Compare current practices against the defined maturity levels to determine areas for improvement.
7. Develop Improvement Plans
Based on the gaps identified, develop targeted improvement plans for each domain. Plans should include short-term and long-term initiatives to enhance the organization's resilience against ransomware.
8. Implement, Monitor, and Review
Implement the improvement plans, continuously monitor their effectiveness, and review the organization's progress towards higher maturity levels. Adjust strategies as necessary based on evolving threats and business objectives.
9. Stakeholder Communication
Regularly communicate progress, risks, and achievements to stakeholders, including executive management, to ensure continued support and alignment with the organization's overall risk management strategy.
10. Continuous Improvement
Incorporate lessons learned from assessments, incidents, and industry developments into the maturity model. Continuously refine the model to address new ransomware tactics and techniques.
Creating a maturity model for ransomware preparedness is an iterative process that helps organizations systematically improve their cybersecurity posture, reduce their vulnerability to attacks, and enhance their ability to respond to and recover from incidents.